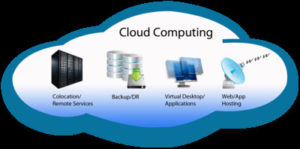
Just because its free does not mean it is good for you. I remember the saying, “You get what you pay for.” What is the Cloud? Cloud is the term that describes a server somewhere out on the internet that you do not own that hosts something of yours. Examples: Microsoft One Drive, Google Drop […]
ID Theft and Your Security
Holidays come with a price. Don’t let your guard down. You need to protect yourself and your identity. Let’s start by keeping track of your personal documents. Try not to dismiss simple things like credit card offers and or bills. Don’t just throw them away. Shred or destroy them. In the wrong hands they can […]
UBUNTU
I have to hand it to UBUNTU for coming out with a decent operating environment. I am ever the pessimist but take it lightly. 1. When it finished installing the screen was dimmed all of the way off. 2. Had to run a bunch of terminal commands to edit 2 separate config files just so […]
Drive By Banner Ads – An Effective Way to Give You a Virus. Who Knew?
Today I am taking some time to touch on a topic that never gets any press. No major companies who have advertisers want to say anything about it. That would make them responsible! Here it is. The people who write malicious viruses that damage computers and steal identities are making a lot of money these days. They […]
A couple new features
I was looking around and decided to add a share link and a voting link. I am trying to get more traffic so please comment on everything. Don’t be forgiving. Just put it out there. If it creates an issue I will “adjust” the comment … like this … but, I will be sure to […]
Put the word out
Tell your family and your friends we are here. Get them to go to the Ask MT page with questions. We need as many as you can throw our way!
Welcome to our official blog
Welcome to our official blog site. Please allow us some time to get this page organized the way we would like it to be. Any attention you can send our way would be very much appreciated. Specifically to our FAQ page. We are gunning to get that page to take off and have a life […]