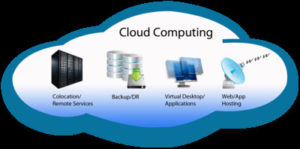
Just because its free does not mean it is good for you. I remember the saying, “You get what you pay for.” What is the Cloud? Cloud is the term that describes a server somewhere out on the internet that you do not own that hosts something of yours. Examples: Microsoft One Drive, Google Drop […]
Cleaning up a compromised Edge Browser

The Edge browser is from Microsoft for windows 10 and server 2016. They advertise that it is more secure and that it has improved performance. You can hit the blogs and learn that everyone is having the issues. But what if you do? If your edge browser gets compromised start by going to the top right and […]
Antivirus: DO YOU HAVE IT
Make sure you do have antivirus and that it is up to date. Also verify you have a backup plan and that you have a current backup. There is a new virus out and it is Nasty. Besides stealing your information, it also encrypts your files. They ask you to pay to decrypt. That apparently […]
ID Theft and Your Security
Holidays come with a price. Don’t let your guard down. You need to protect yourself and your identity. Let’s start by keeping track of your personal documents. Try not to dismiss simple things like credit card offers and or bills. Don’t just throw them away. Shred or destroy them. In the wrong hands they can […]
The Small Things Matter
I am using my phone for this one so I need to keep it simple. A lot of small needs came through the door this week. The devil is in the details. One browser hijack, one “lost” app, an email client imap issue, and a computer tweak over a remote support session. There were many […]
Drafting Division

One of my business customers called today with a printer issue. It simply was not working. The printer was located in the drafting department. These guys are some of the highest paid in the company because their work generates bids on work that enterprise customers of the company will hopefully accept. I try to keep […]
Dell Netbook (Inspiron Mini) with a virus
I received a very interesting call today. This customer called in from about an hour away and said that he had a Dell Net book that he purchased from a friend and it had a virus. He wanted to know if I could fix that. So I met him for lunch at a local restaurant and […]
Welcome to our official blog
Welcome to our official blog site. Please allow us some time to get this page organized the way we would like it to be. Any attention you can send our way would be very much appreciated. Specifically to our FAQ page. We are gunning to get that page to take off and have a life […]