Free consult, Free Pickup, Free Delivery, 30 day guarantee on the work. And I get to see the sun set.
We no longer resell equipment for Ingram and no longer maintain an EIN with the FED.
Midnight Tech as a business was established in 2003. I originally opened it because I felt I wanted to give people IT support at affordable rates. I am honest. I never did take advantage of anyone. But I fairly charged everyone. For these reasons, MT did not bring in a lot of money. I did […]
Plan for future success.
Do you have a Incident Response Plan? This type of plan contains the steps you would take before anything happens that would threaten your security. It ensures you can respond quickly and correctly to address the issue and prevent future instances. Do you have a Business Continuity Plan? This plan is created when Incident Response […]
Asia
No disrespect to the wonderful people of Asia. These people are wonderful. Descended from SHEM, an Asiatic, and the son of NOAH. Today I was working on the store. A past time that was at one time much more interesting and enjoyable. I did go and work for an Insurance agency and a Point of […]
CLOUD “Email, Social Media, Hosting, and Applications” all have a drawback…
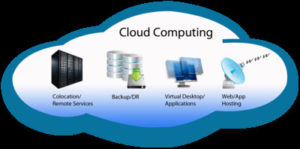
Just because its free does not mean it is good for you. I remember the saying, “You get what you pay for.” What is the Cloud? Cloud is the term that describes a server somewhere out on the internet that you do not own that hosts something of yours. Examples: Microsoft One Drive, Google Drop […]
Power Outage

Perhaps, all technology that you use depends on power provided to you by your utility provider. Storing energy is not enough. You need to replenish the energy that is used in order to have energy to use. Where do you get energy from? How do you store it? What do you depend on that requires […]
Marketing all goes back to LOGO

Everything about identity creation leads back to a logo. We do not think about it’s importance and many take a logo for granted. My last logo was created by JAC out of Marion IL a very long time ago. It was a great design and has served very well. Impressive work. During these many years […]
Website Work
Website owners need their website to represent them to the world by displaying what they do in a clear concise manner. It should present well on a phone, a tablet and on a computer. It must be secure, easy to read, simple to navigate, and offer easy methods for the visitor to make contact. It […]
Hacks, Attacks, and your VOICE
Online CRIMINAL activity? What is going on these days with spam, email and social media profile hijacking? Why is this such a thing? For a business this is a big deal! I keep mentioning haveibeenpwnd.com. This is a database of companies and customers of companies that were compromised. Put your email in to see if […]
